Platform > Ignite > PHYSICAL SECURITY INTELLIGENCE
Flashpoint Physical Security Intelligence
Enhance situational awareness with real-time geo-enriched data and intelligence expertise.
With an expanding online communication landscape, security and intelligence teams face an increasing volume of data but lack the tools to effectively separate the threats from the noise.
Flashpoint Physical Security Intelligence (PSI) delivers geo-enriched data and finished intelligence from an extensive, global range of open sources like social media, messaging apps, defense forums, and illicit communities. Customers can easily translate, analyze, and monitor the data to understand critical events, geopolitical situations, and executive threats.

Global open-source intelligence (OSINT), 24/7 monitoring, and critical alerts to protect people, places, and assets
Accelerate investigations and enhance situational awareness with open-source data, intelligence expertise, analytical tools, and AI enrichments. Effortlessly filter out social media noise to extract meaningful information quickly, monitor the topics and locations that matter to your organization, and ensure the right team members are alerted when relevant posts are detected.
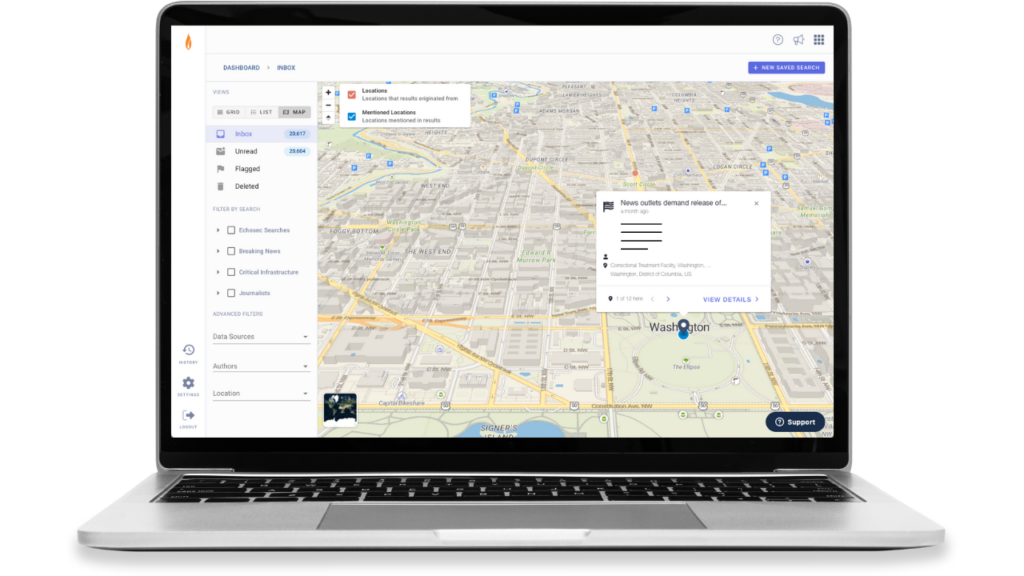
Increase situational awareness
With streamlined access to an extensive range of open-source data and geospatial enrichments, PSI provides unmatched visibility and context into situations happening anywhere in the world, to help our customers safeguard their people, places, and assets.
Extend your team's capacity
Leverage integrated AI, automated threat actor insights, and advanced filters to get more work done, faster. Alleviate the strain on your time, resources, and skills, with one-click access to Flashpoint’s expert intelligence team.
Accelerate speed-to-insight
Get meaningful results within seconds of the data appearing online. Monitor events as they unfold, so you can make timely decisions based on changes in the information environment.
Supporting critical workflows for Physical Security teams
Streamlined investigations
Harness the power of social media to shine a spotlight on a specific location, situation, and time frame. Leverage actor insights to instantly develop an understanding of threat actor behavior and analyze patterns of life.
Executive protection
Quickly and easily build search criteria to monitor key personnel during high-profile events, while traveling, or in day-to-day life. Be alerted to potential dangers so you can swiftly take action.
Event/crisis monitoring
Gain unparalleled situational awareness with real-time information about incidents near your business or supply chain locations. Leverage integrated AI to rapidly gather insight and context around events to better understand what happened, and how to respond.
Threat assessment
Gather intelligence on potential threats to your organization, key locations, and personnel. Understand and assess extremist activity, public disruptions, natural disasters, and geopolitical situations.
See for yourself!
Additional offerings
"The tool allows us to stay up to date with any online threats made against our clients or simply general public discourse surrounding our client's image. We utilize the saved searches feature which include various filters to help us find the most threatening chatter and alert ourselves to any issues that may require immediate attention."
-SECURITY & INVESTIGATIONS PROFESSIONAL
