Blog
Digital Risk Management: Why Integrating Corporate Teams Is Crucial
Why is cross-enterprise functionality necessary to manage digital risk, and how can this approach be adopted?

Some of the most damaging threats to any enterprise—from data leaks to PR disasters—can now be identified on the open, deep, and dark web.
To address digital risks quickly and minimize hefty fiscal and reputational damages, organizations are turning to digital risk management and protection technologies to keep their digital footprint secure.
Differentiated from traditional threat intelligence strategies, digital risk protection is emerging as a comprehensive business strategy. Beyond an organization’s cybersecurity team, digital risk management solutions are also valuable for marketing, compliance, HR, and even physical security teams as the online risk landscape diversifies.
But existing digital risk management solutions often fail to address these org-wide applications. Commercially-available solutions are often rooted in conventional threat intelligence tooling, which tends to be designed for technical security users and individual user workflows.
Why is cross-enterprise functionality necessary to manage digital risk, and how can this approach be adopted?
What is digital risk management?
Digital risk management solutions enable organizations to uncover threats to their digital assets and brand on the open, deep, and dark web. Digital transformation has rapidly expanded this requirement as more organizations widen their attack surface by adopting the cloud, social media, and other online platforms. Digital risk solutions help reduce negative business impacts, providing organizations with a holistic protection strategy for threats to their online footprint. This differs from traditional threat intelligence services, which focus on integration and analysis of threat data feeds, often for highly technical users.
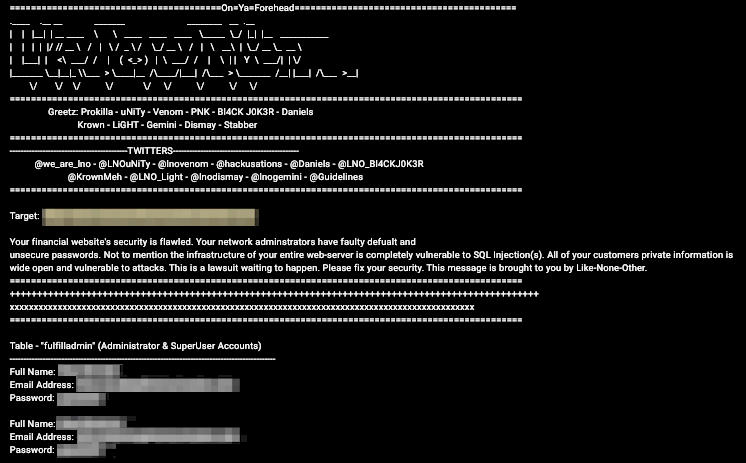
The goal of a digital risk management solution is to monitor an organization’s external risk environment easily and efficiently for brand-name and other digital asset mentions. Users can also track broader trends and threats targeting an industry. Digital risks could include indicators of a data breach, fraud, brand impersonation, and intellectual property theft.
Who benefits from digital risk management?
One of the key differentiators between digital risk management solutions and traditional threat intelligence tooling is its appeal to a number of roles across corporate environments.
For example, digital risk management applies to:
- Cybersecurity teams—locating cyber threats like data leaks, phishing attempts, targeted malware, account takeovers, fraud, and credential theft
- Marketing—identifying brand risks, including damaging viral content, negative sentiment or public response to a company, fake websites/profiles and impersonation, and disinformation implicating a company
- Compliance—assessing data leaks and managing their impacts, both for the company and any third party
- Physical security—monitoring physical assets via social media, ensuring executive safety during travel or high-profile events, overseeing threats to supply chain locations, and identifying physical risk indicators online (such as an active shooter scenario)
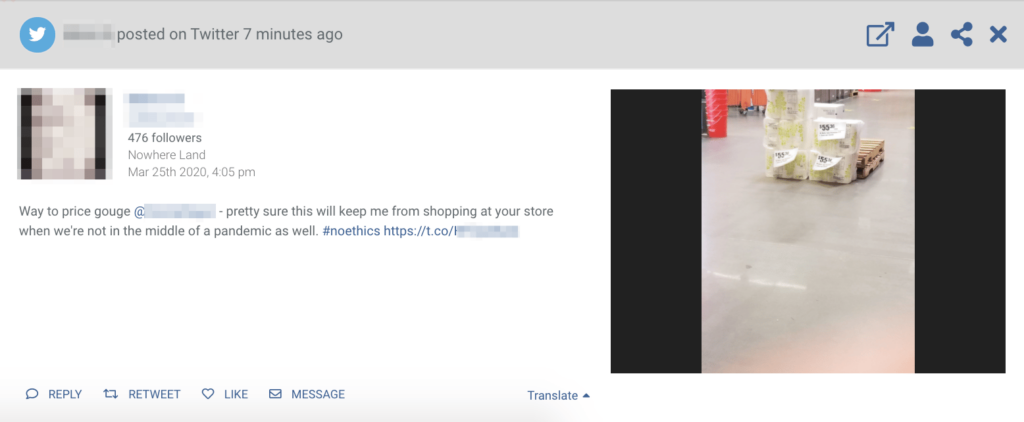
The risk of disconnecting corporate teams
Digital risk solutions make up a relatively emerging market. Existing tools and services vary in their approach and niche when it comes to data coverage and product design. The shift to understanding digital risk management as an org-wide business strategy is a new perspective in the corporate security world, and functional gaps remain to be bridged in product offerings.
Digital risk management is not yet well-defined as a cross-enterprise strategy separate from other threat intelligence technology. Even though solutions are now applicable to multiple business departments, they aren’t always optimized for cross-enterprise adoption.
For example, tools may lack user-friendly interfaces for non-technical departments like marketing and compliance. Solutions designed around uncovering technical risks can make other business impacts less visible to non-technical users, resulting in lost org-wide buy-in and adoption. Traditional threat intelligence solutions also tend to empower individual user workflows rather than enabling collaboration between teams or corporate departments. In the event of a serious threat like a data breach, an entire organization is affected—from finance to marketing. A siloed approach stifles an organization’s progress towards understanding digital risks as business-wide risks. This can result in blind spots where use cases overlap enterprise roles, disrupting effective crisis response.
Adopting integrated risk management
So how do corporate security managers support an org-wide approach in their digital risk strategy?
This often boils down to their choice of digital risk management service provider and the use of features that enable cross-enterprise usability and collaboration. This could be as simple as prioritizing a user-friendly interface intuitive enough for non-technical users—while retaining the depth of data required for cybersecurity teams.
Collaboration and usage permission features also allow organizations to view or collaborate on their digital risk protection strategy more effectively within or across corporate teams.
For example, Flashpoint offers a range of tools to monitor digital assets in real-time. Administrators can organize assets into groups defined by private, view-only, or edit permissions. This allows teams to more easily track and collaborate on digital risk management, or keep private projects hands-off when necessary.
These types of features help set apart org-wide digital risk strategies from a disconnected approach, supporting a more holistic solution.
When multiple departments are implicated in digital risk management (as they usually are today), teams can collaborate seamlessly and uncover more valuable intelligence and context than is available through a siloed approach.
At a high level, this approach also supports an organization’s shift from understanding digital risk as an IT problem to understanding it as a broader business concern. As the online attack surface increases for most organizations, this will make the difference between successful digital crisis response—or unrecoverable damages.

