Platform > IGNITE
Flashpoint Ignite Platform
Connect, collaborate, and remediate risk faster with timely and active intelligence. Gain visibility into intelligence landscapes across cyber threats, vulnerabilities, and physical security. With Ignite, security experts can connect the dots across data and intelligence to coordinate a better informed, more effective response–with a holistic view of risk in one place.

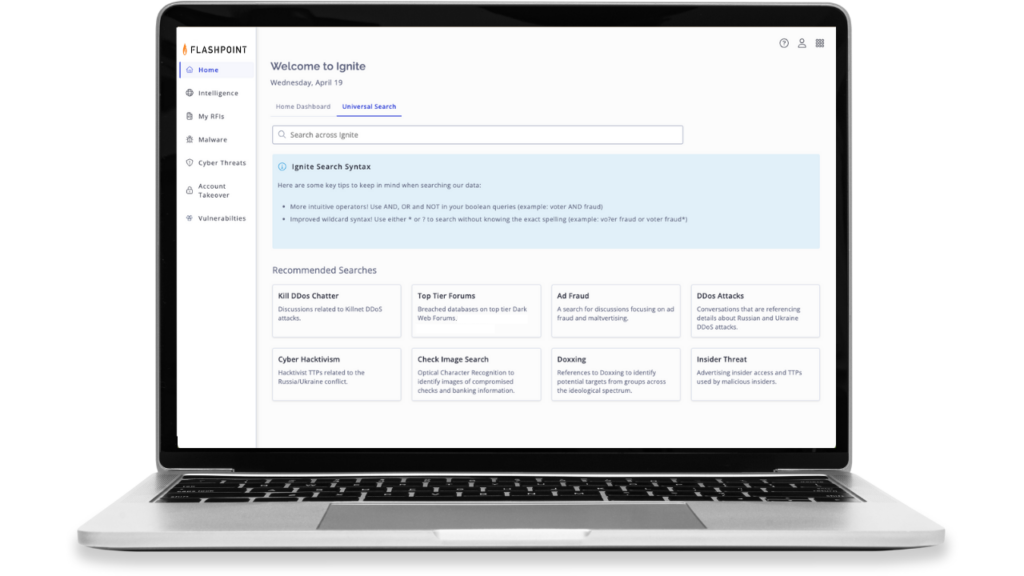
Achieve more with one platform
Easily obtain the information you need and seamlessly work across multiple teams to move information forward and remediate risk faster.
Dependable intelligence for everyone
With visibility into the deep and dark web, OSINT/surface web, vulnerabilities, breach data, or geospatial intelligence, our finished intelligence reports and raw collections are right at your fingertips so you can spend your time on what matters most.
Close the gap between data, intelligence, and action
Quickly assess your data and intelligence outcomes across all products, streamline workflows, adapt and take decisive action to stay ahead of the changing threat landscape.
