GLOSSARY
What Is Threat Intelligence?
Whether you’re a newbie, a practitioner, or CISO who wants to deepen your understanding of threat intelligence—we’ve got you covered.

Introduction to threat intelligence
Why has threat intelligence (TI) become essential to so many organizations around the globe? If you’re reading this you’re likely seeking a deeper and more current understanding of threat intelligence and its practical applications.
You’ve come to the right place.
Whether you’re a newbie who wants to understand the Venn diagram of threat intelligence and cyber threat intelligence (CTI), or the overlap of cyber and physical threats; or a practitioner who wants to unleash the power of open-source intelligence (OSINT) or gain a better understanding of the dark web; or a CISO who wants to integrate threat intel into your security operations to better protect your data, assets, infrastructure, and stakeholders—we’ve got you covered.
What is threat intelligence?
Threat intelligence refers to the knowledge, context, and insights gained from analyzing a broad spectrum of physical, geopolitical, and cyber threats. Security teams collect, analyze, and interpret threat intel to understand the tactics, techniques, and procedures employed by threat actors.
Threat intelligence is foundational to your organization’s overall security posture. It helps teams identify and mitigate potential threats to the safety of an organization’s assets, systems, data, infrastructure and people.
Threat intelligence vs. Cyber threat intelligence
The terms threat intelligence and cyber threat intelligence (CTI) are often used interchangeably—but they have distinct nuances. Threat intel encompasses all threats across the physical, a broad spectrum of risks, including physical, geopolitical, and cyber threats. However, CTI specifically hones in on the identification and analysis of digital threats and attacks.
As risks overlap and threat actors leverage new attack vectors, the worlds of physical and cyber threats are converging. It’s critical for organizations to understand how cyber threats can become physical threats, and vice versa. It is also important to have strong intelligence capabilities that support both fronts of the threat landscape.
Threat intelligence vs. External threat intelligence
Threat intelligence spans across both internal and external sources of information. External threat intel specifically refers to insights gathered from sources outside the organization. This includes open-source intelligence (OSINT) and intelligence derived from the deep and dark web.
External threat intelligence supplements internal data and provides a wider context for organizations to understand the evolving threat landscape and make informed decisions to strengthen their cyber and physical security defenses. It provides organizations with a broader perspective on the threat landscape, helping them understand emerging threats, new vulnerabilities, and attack trends that may impact their security.
Types of threats
Threat actors continue to find new ways to exploit vulnerabilities and leverage security weaknesses to attack.
Common cyber threats
- Malware: Malicious software designed to infiltrate systems, steal data, or cause harm.
- Phishing: Sending fraudulent emails or messages to trick users into revealing sensitive information.
- Ransomware: Malware that encrypts a user’s data and demands a ransom for decryption.
- Denial of Service (DOS) and Distributed Denial of Service (DDoS) Attacks: Overloading a system or network to render it unavailable.
- Insider Threats: Malicious actions from within an organization by employees, contractors, or partners.
- Social Engineering: Manipulating individuals into divulging confidential information or performing actions.
- Advanced Persistent Threats (APTs): Long-term targeted attacks by well-funded and organized threat actors.
- Zero-day Exploits: Attacks leveraging vulnerabilities unknown to the software vendor.
Common physical threats
- Terrorism: Acts of violence targeting people, property, or infrastructure to create fear and disrupt operations.
- Physical theft: Unauthorized taking of physical assets, equipment, or valuable items from the organization’s premises.
- Supply chain disruptions: Disruptions in the supply chain due to events like natural disasters, political instability, or transportation issues.
- Cyber-physical attacks: Coordinated attacks targeting both cyber and physical assets, such as industrial control systems and critical infrastructure.
- Social unrest and civil disturbances: Protests, riots, or other forms of social unrest that can lead to property damage and potential violence.
- Workplace violence: Threats or acts of violence within the workplace that can endanger employees and disrupt operations.
- Unauthorized access and intrusions: Breaches of physical security measures, including unauthorized access to facilities, restricted areas, or systems.
- Critical infrastructure attacks: Targeting of critical infrastructure sectors, such as energy, transportation, and telecommunications.
Why is threat intelligence important?
Threat intelligence provides cybersecurity and physical security practitioners, stakeholders, and executives with valuable insights and actionable information to enhance their security posture and safeguard their people, assets, and data.
For practitioners, a threat intelligence program enables them to proactively identify and understand potential threats, vulnerabilities, and attack techniques. By leveraging timely and accurate intelligence, practitioners can effectively prioritize and allocate resources to mitigate risks, strengthen defenses, and respond swiftly to emerging threats. It empowers them to make informed decisions, enhance incident response capabilities, and stay one step ahead of cyber adversaries.
For stakeholders and executives, a threat intelligence program offers a broader perspective on the cybersecurity landscape. This enables them to comprehend the potential impact of threats on the organization’s overall business objectives and reputation. Threat intelligence provides them with critical contextual information, including the tactics, techniques, and procedures employed by threat actors, emerging trends, and industry-specific risks. This knowledge allows stakeholders and executives to make strategic decisions regarding risk management, investment in security technologies, and resource allocation.
Staying ahead of threat actors
As threat actors become more advanced in their ability to leverage attacks against specific companies or industries, it’s crucial for organizations to advance their own threat intel capabilities accordingly, in order to successfully defend their assets and infrastructure. A thorough understanding of your own threat landscape is required to know which tools and technology are needed to properly identify, prioritize, and combat risks.
A large part of threat intel is knowing where to look for information. This has become more challenging as the channels through which threat actors operate diversify, although a large number of illicit communities use the deep and dark web to act—which means your security teams must be familiar with this obscure and often misunderstood part of the online world.
Knowing how your organization may be targeted—via what we call “risk apertures”—is also necessary to proactively avert attacks. Threat actors change approaches depending on what they’re trying to achieve. Their attempts range from brute forcing, credential stuffing, to exploiting vulnerabilities and ransomware. It’s imperative that security teams are prepared.
Threat intelligence use cases
Enriching your organization’s security posture
The ways threat intel can benefit your team or organization depend on your role and objectives. Perhaps most importantly, a solid threat intel process allows you to enrich the security posture of your entire organization, all the way from policy development to incident response and remediation plans. The better your understanding of the threat landscape, the better prepared you can be to respond to the latest threats. To this end, including threat intel in the use of other tools augments the value they provide as well.
Contextual insights and analysis
Threat intel also assists in the prioritization of threats, lending valuable insights into how a certain risk may play out for your organization. If an attack does happen, analysis of its status and impact is also enhanced using the intelligence your teams have on the who, what, and how of the situation.
Proactive threat hunting
Just as threat hunting is a required part of your threat intelligence, threat intelligence is required for threat hunting. Use threat hunting to expose previously unnoticed compromises and proactively stop attacks that target your data and infrastructure.
Incident response
In the event of a security incident, integrating threat intel into your incident response plan enables you to swiftly identify the nature of the threat, its origin, and its potential impact. This allows your incident response teams to make informed decisions and execute a coordinated response, minimizing downtime and reducing the potential damage. The real-time insights gained from threat intelligence enable your teams to take appropriate actions, contain the threat, and recover more effectively.
Vulnerability management
Effective vulnerability management is a cornerstone of any robust cybersecurity strategy. Threat intel empowers your organization to proactively identify vulnerabilities that could be exploited by malicious actors. By staying informed about emerging vulnerabilities and their potential exploits, your vulnerability management teams can prioritize patching and mitigation efforts. This not only reduces your attack surface, but also strengthens your overall security posture, making it significantly harder for attackers to breach your defenses.
Security operations
Integrating threat intelligence into your security operations center (SOC) operations amplifies your ability to detect, analyze, and respond to threats in real-time. By continuously monitoring and analyzing threat intel feeds, your SOC teams can detect and thwart attacks more effectively. This intelligence enables your analysts to correlate incoming data with known threat indicators, identify patterns, and uncover hidden connections, allowing for a more comprehensive understanding of the threat landscape.
Risk assessment and mitigation
Threat intelligence serves as a valuable resource for conducting accurate risk assessments across your organization’s digital ecosystem. By leveraging threat intel-related data, you can evaluate potential risks more holistically and assign appropriate risk scores. This enables your risk management teams to make informed decisions about resource allocation, investment in security measures, and the implementation of targeted risk mitigation strategies.
Threat intelligence challenges
While the benefits of threat intel are substantial, organizations often encounter challenges in its effective implementation. These challenges include:
- Data overload: The sheer volume of intelligence-driven data can overwhelm teams, making it crucial to employ robust analytics and automation tools to process and prioritize the information.
- Quality and relevance: Ensuring the quality and relevance of threat intelligence sources is essential to avoid basing decisions on outdated or inaccurate information.
- Integration complexity: Integrating intelligence into existing security tools and processes requires careful planning to ensure seamless collaboration and data sharing.
- Skill gap: Navigating the intricate world of threat intel requires skilled personnel who can interpret and apply the insights effectively.
- Resource constraints: Adequate resource allocation is necessary to fully leverage threat intel and implement necessary changes across the organization.
The three types of threat intel
Each of the three types of threat intel serve a different function in combating emerging threats and cyber attacks. Strategic, operational, and tactical threat intelligence all play complementary roles in building a comprehensive defense plan that successfully manages the risks your organization faces.
- Strategic threat intelligence: Provides a high-level look at the threat landscape, giving visibility into how it evolves over time.
- Operational threat intelligence: Focuses on specific attacks that an organization is at risk for in real-time.
- Tactical threat intelligence: Concerns itself with information about the tactics, techniques, and procedures (TTPs), and Indicators of Compromise (IOCs), that are needed to build a defense plan.
Five stages of the threat intelligence lifecycle
Threat intelligence encompasses the entire process of dealing with threats and it can be broken into five stages that define each step in the journey:
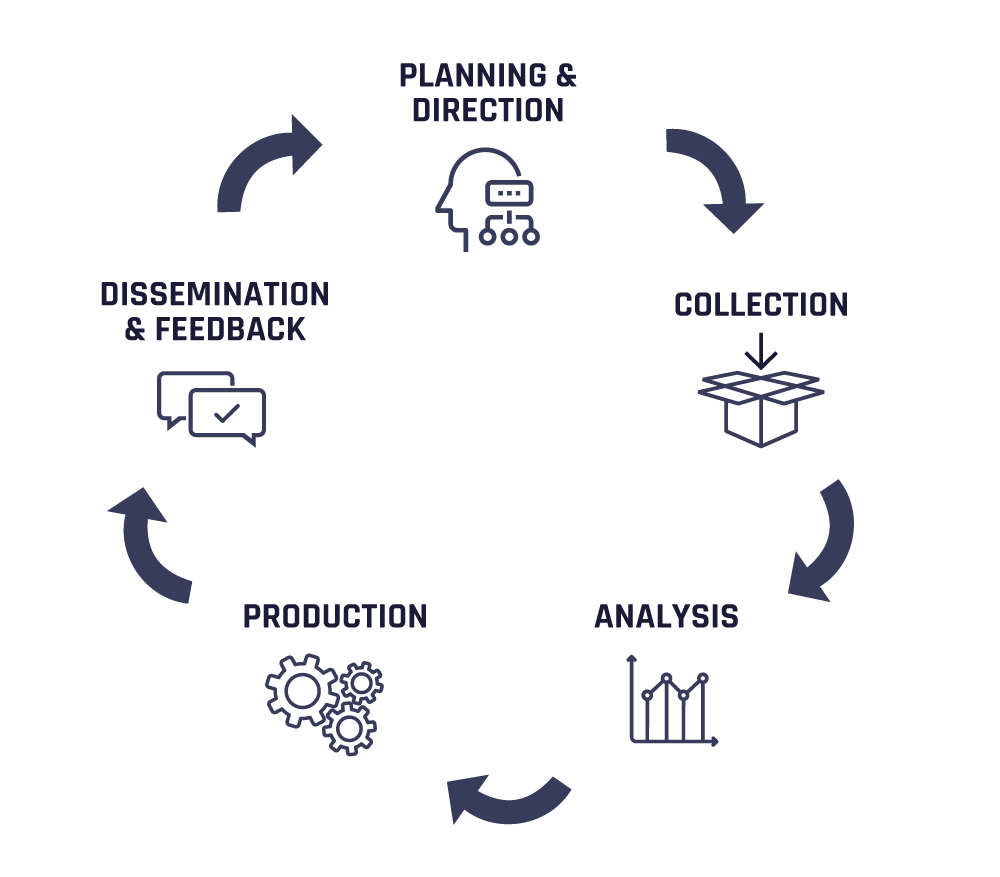
- Planning and direction: Set the scope and objectives for core intel roles and processes.
- Collection: Deploy data gathering and processing techniques and sources.
- Analysis: Translate raw intel into meaningful and taxonomized actors, events, and attributes.
- Production: Assess intel significance and severity based on business and environmental context.
- Dissemination and feedback: Report on finished intel, considering urgency and confidentiality.
Leverage Flashpoint to bolster your threat intelligence capabilities
Any organization’s security capabilities are only as good as its threat intelligence. Flashpoint’s suite of tools offer you a comprehensive overview of your threat landscape and the ability to proactively address risks and protect your critical data assets. Get started with a free trial to unlock the power of great threat intel.

