Blog
The Complete Holiday Shopping Threat Landscape
This blog is part of our 2022 Year In Review, an intelligence retrospective highlighting the most significant trends of the past year—plus insight into 2023.

‘Tis the season… for gifting. Even though Black Friday and Cyber Monday are behind us, the shopping season began back in October and will continue into January, when returns become a major factor.
‘Tis also the season… for threat actors to exploit consumers and retailers alike, and leverage a variety of tactics for financial or ideological gain.
‘Tis also the season … for security teams to be prepared to combat fraud and prepare to protect their online ecosystems and physical locations.
In this article, we cover the holiday shopping season threat landscape—plus the major economic, social, and political factors that could impact one of the busiest times of the year. Finally, we offer mitigation strategies and best practices.
Cyber threat landscape
According to Adobe, e-commerce sales are not likely to increase at rates observed during previous holiday shopping seasons. This is most likely due to inflation: Online shopping steadily increased in the earlier months of 2022, but were eventually curbed as other costs—like housing and gas—rose in the later months of the year. Despite this, financially-motivated threat actors will almost surely still attempt to exploit retailers and customers.
Related Reading: Physical Security Threat Assessment: Holiday Edition
Social engineering
Retailers are pulling out all the stops to incentivize spending, especially for electronics, sporting goods, toys, and appliances, including a high volume of discount codes. As a result, threat actors will likely tailor social engineering campaigns, like phishing emails or smishing (SMS phishing) messages, to masquerade as retail discounts in order to steal sensitive customer information like account login credentials or financial information. Last year, IKEA dealt with ongoing internal phishing attacks between Black Friday and Cyber Monday.
Ransomware
Since January 2022, Flashpoint has identified 45 data leaks from retailers around the world posted to ransomware gangs’ leak sites, as of this publishing. Victim data is leaked if the ransom is not paid to the ransomer by a predetermined time. This also means that this data only covers instances in which the ransomers’ demands were not met, making it highly likely that other retailers were targeted by ransomware attacks and paid the ransom so that their information would not be leaked.
“Ransomware gangs and affiliates will likely target retailers based on the assumption that their victims will be more likely to pay a ransom, in order to minimize downtime and keep their names off leak sites.”
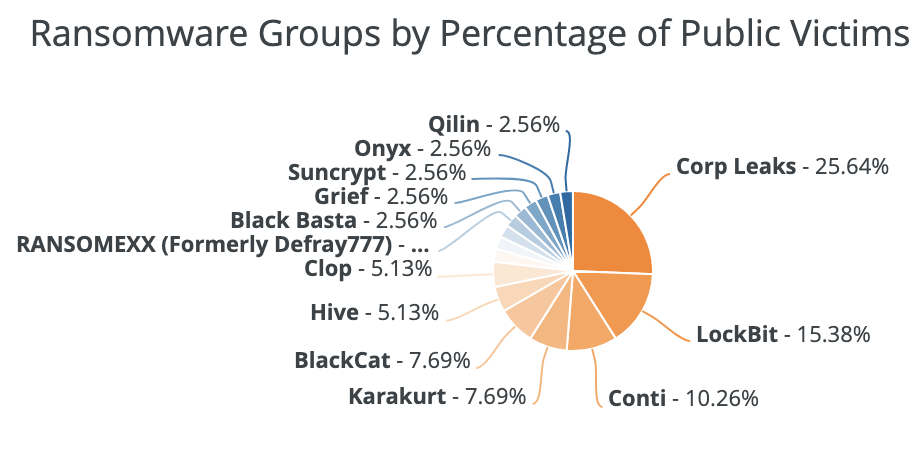
During last year’s holiday shopping season, which Flashpoint defines as the period between October 2021 and January 2022, a total of 20 retailers were posted on ransomware leak sites, with Conti and LockBit being the largest perpetrators. For comparison, in all of the months prior in 2021 (between January and September), Flashpoint observed 34 ransomware attacks. This indicates an increase of attacks during the holiday season, with an average of roughly 32 percent more attacks per month throughout.
Based on this trend, it’s likely that retailers may experience an increased threat of ransomware attacks during the October 2022-January 2023 period. Ransomware gangs and affiliates will likely target retailers based on the assumption that their victims will be more likely to pay a ransom, in order to minimize downtime and keep their names off leak sites. Otherwise, these attacks could greatly diminish overall profitability.
Historically, ransomware gangs have carried out attacks on holiday weekends, when employees are out of the office and the response times for detecting and mitigating cyber threats may be longer.
Curbside pickup fraud
The holiday shopping seasons of 2020 and 2021 saw the advent of curbside pickup fraud services, as retailers implemented safeguards and policies to limit customer and employee interaction during the COVID-19 pandemic. According to Adobe, curbside pickups will likely spike between December 22 and 23, and that overall, 35 percent of shoppers plan on using curbside pickup during the holiday shopping season.
While “curbside methods” are still being discussed and advertised, increased difficulty in facilitating this fraud makes it likely that threat actors may prioritize other fraud tactics.
Original iterations of this fraud depended on the fact that interactions between employees and customers had to be minimal for health and safety reasons. This enabled the individual picking up the order to obfuscate their identity. As these restrictions are no longer implemented, this fraud may be perceived as being riskier than other types of fraud.
Regardless, curbside fraud will likely still be a threat to retailers this holiday shopping season, although the tactics may be less refined than in previous years.
Refund fraud
Threat actors participating in refund fraud seek to take advantage of retailers’ return policies, customer service representatives, and third-party affiliates to receive fraudulent refunds for goods.
Since October 1, the most popular refund fraud methods discussed and advertised within Flashpoint collections have been the “partial refund” method and “fake tracking ID” method.
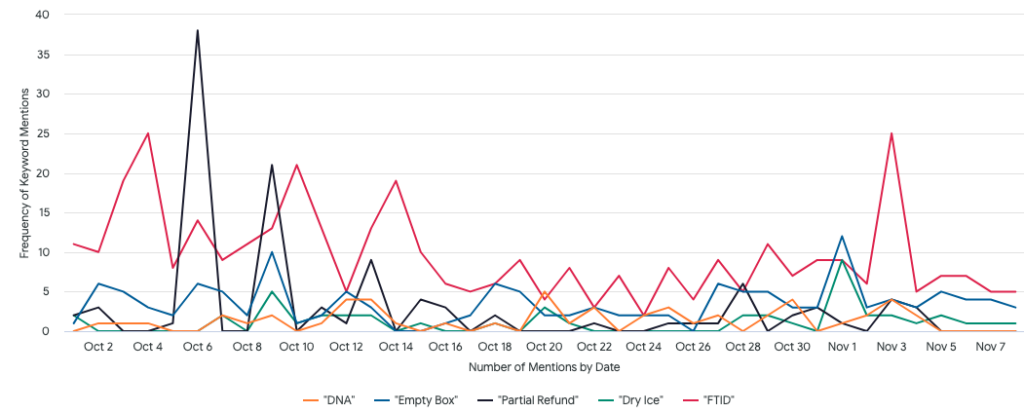
Last year, the most discussed and advertised refund method was by far the fake tracking ID method, followed by the “empty box” method and the partial refund method.
According to the National Retail Federation (NRF), $761B in returned goods over the entirety of 2021, approximately 10 percent ($78.4B) were deemed fraudulent. The report also noted that the majority of returned items, fraudulent and legitimate, are from online orders.
Holiday shopping data in this report was collected between October and November 2021, and therefore does not encompass the entirety of the holiday shopping season. Between October and November 2021, consumers spent approximately $887B, and $158B of that merchandise was returned. Of those total returns, $17B was identified as fraudulent, accounting for approximately 10 percent and mirroring statistics from the entirety of 2021.
Gift card fraud
Threat actors often buy high-priced gift cards to use at a later date. Gift cards can be purchased with compromised financial information or through compromised retail accounts where credit card information is stored. Gaining access to retail accounts is most likely done through phishing attacks, password-spraying attacks, or other brute-force and social engineering attacks.
Some actors advertise gift card services on deep and dark web (DDW) forums and chat services in which they offer to acquire goods at a discount by using the fraudulently funded gift cards. Fraudulent gift cards are also often bundled into advertisements for cash-out services and other financial fraud, as purchasing gift cards is a popular and efficient way to exfiltrate money from a compromised account.
CMS access
Threat actors will likely attempt to exploit retailers’ content management systems (CMS) accesses to harvest customer information stored in CMS panels and plugins, including credit card or payment information.
In many observed instances, threat actors target known vulnerabilities in popular content management systems (CMS) and website plugins including Magento and WordPress’s WooCommerce. Last year, ahead of Black Friday and Cyber Monday, the United Kingdom’s National Cyber Security Centre (NCSC) issued a warning to retailers regarding commonly exploited vulnerabilities in the e-commerce platform Magento. According to the NCSC, the majority of financial skimming attacks take advantage of Magento resources. Threat actors exploit a well-known vulnerability within the platform to launch cyberattacks in which they steal financial data.
Merchandise shortages and delays
With the global supply chain still struggling to recover after the COVID-19 pandemic and related shutdowns, global labor shortages, high rates of inflation, and transportation delays, retailers across the country are likely to experience merchandise shortages or delays throughout the holiday season. As seen in previous years, the heightened tension surrounding holiday shopping combined with customers’ inability to obtain the items they seek will likely lead to an increase in confrontations with retail staff or physical altercations between customers attempting to purchase the same item.
Merchandise shortages are very likely to increase the shipping times of items, which may result in a large number of packages not reaching their intended destination in time for the intended holiday. This may result in customers harassing employees of post offices and delivery services out of frustration over late packages.
Mitigation
Formalized communication channels
Retailers can help mitigate fraud and other cybersecurity issues this holiday season by establishing a clear and formalized communication channel with their consumers. This may manifest as using an official email address or phone number when sending discount codes or updates on stock, or as formalized guidelines as to when and how the retailer may reach out to customers.
Return windows and regulations
In previous years, retailers have been advised to shrink the window of time that they accept returns for merchandise purchased during the holiday season, which could limit the overall volume of fraudulent returns. Of retailers polled in NRF’s report, nearly 83 percent of retailers do not offer and are currently not planning on offering third-party “no box, no label” returns, which should minimize refund fraud.
Patching
Establishing a consistent software vulnerability patching cycle, offering comprehensive employee training, and enabling multifactor authentication (MFA) on customer and employee accounts can assist in mitigating other fraud, like CMS exploitation and social engineering.
Physical security considerations
Large and unruly crowds are an inherent component of “doorbuster” sales, or seasonal sales featuring highly discounted items. As of this writing, Black Friday shopping events since 2006 have led to approximately 17 deaths and 125 injuries. To ensure the safety of employees and customers, Flashpoint advises retail establishments to design, review, and practice store opening procedures before the height of the holiday shopping season.
Implementing the following security measures may increase the safety of retail employees and customers:
- Putting Entry and Exit Controls in Place: Employees are frequently injured during the initial door opening on Black Friday due to stampeding customers. Facilities should ensure that employees can open the doors remotely or from a safe or elevated position. Stores should ensure that customers can only enter through designated entry points; exit, employee, and delivery doors should be secured to prevent unauthorized access.
- Placing Merchandise in a Strategic Way: Strategic placement of merchandise—specifically Black Friday deals—may reduce large pile-ups of customers at entrances, increase traffic flow, and increase visibility on pilferable items. Retailers should consider spreading the sales items throughout the store and keeping these items clear of checkout counters to reduce customer density in high-traffic areas.
Protect your customers and your organization this holiday season with Flashpoint
Flashpoint’s suite of actionable intelligence solutions enables organizations to proactively identify and mitigate cyber and physical risk that could imperil people, places, and assets. To unlock the power of great threat intelligence, get started with a free Flashpoint trial.


